This article describes how to capture traffic between a client and the network with a passive “Man in the Middle”. Also it explains how to generate traffic from a VM where the network only sees 1 MAC and 1 IP address form the client PC.
In the example below, we use eth0 and eth1 as a bridge. In this example, be aware of the client side and network side.
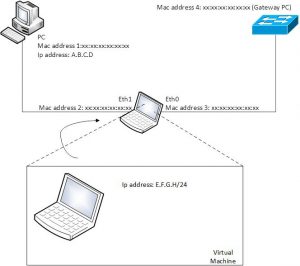
See the following article to build the bridge as a MitM.
Configure the bridge (br0) with an IP address.
- ifconfig br0 X.X.X.X/Y (necessary for iptables nat i.e. 192.168.1.1/24 )
Clear iptables
- iptables -F
iptables -X
iptables -t nat -F
iptables -t nat -X
iptables -t mangle -F
iptables -t mangle -X
Layer 2 source NAT all outgoing traffic towards switch to Mac address of PC.
ebtables -t nat -A POSTROUTING -o eth0 -j snat –to-src <Mac address 1>
Layer 3 ip source NAT all outgoing traffic towards switch to IP address of PC.
iptables -t nat -A POSTROUTING -o TAP -j SNAT –to-source <IP address PC>
To activate iptables on the bridge
- modprobe br_netfilter
- echo 1 > /proc/sys/net/br0/bridge-nf-call-iptables
Start you virtual machine on the MitM
Be sure, you connect your VM to the same interface as the PC and put it on bridge mode
Configure the interface on your VM: ifconfig enp0s3 192.168.1.2/24
Configure a static ARP on your VM with the MAC address of the GW of the PC: arp -s 192.168.1.1 <Mac address 4>
Why?
We want to sent traffic through the bridge, not to the bridge. Note, the ip and mac address on br0 is bogus and not used.
Configure default route on your VM: route add -net default gw 192.168.1.1
Now traffic from the VM to the network is modified on the bridge on layer 2 and layer 3. The source mac address is translated by ebtables. The source ip address is translated by iptables. Note, traffic from the client PC towards network is also “modified” by the bridge but you probably won’t notice it. Iptables keeps track of all connections and knows which connection belongs to the VM and which to the client PC.
Note: any actions you take upon the information in this article is strictly at your own risk!