This article describes how to capture traffic between a client and the network with a passive “Man in the Middle”. In the example below, we use eth0 and eth1 as a bridge. 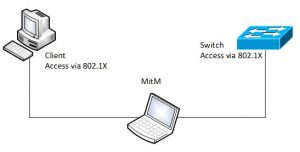
Configure the MitM interfaces as “link only” interfaces.
/etc/network/interfaces
auto eth0 iface eth0 inet manual
auto eth1 iface eth1 inet manual
bring physical interfaces up
- ifconfig eth0 up
- ifconfig eth1 up
clear ip addresses on physical interfaces
- ip addr flush eth0
- ip addr flush eth1
Configure the MitM interfaces as an bridge
build bridge
- brctl addbr br0
- brctl stp br0 off (turn off spanning tree)
- brctl addif br0 eth0
- brctl addif br0 eth1
bringing bridge up
- ifconfig br0 up
Clear and flush ebtables
- ebtables -F
- ebtables -t nat -F
disable traffic from bridge itself
- ebtables -A OUTPUT -s <mac address interface eth0 bridge> -j DROP
- ebtables -A OUTPUT -s <mac address interface eth1 bridge> -j DROP
- ebtables -A OUTPUT -s <mac address interface br0> -j DROP
In case of 802.1X network access, to forward EAP messages on MitM:
echo 8 > /sys/class/net/br0/bridge/group_fwd_mask
Now we can start Wireshark on MitM and capture traffic on eth0, eth1 and/or br0.