you have a remote ssh server with tcpdump or dumpcap installed.
From a client which has ssh access to the remote server, you can run wireshark on the client and capture live traffic remote.
In case the user needs sudo to capture, wireshark will not prompt for the password. So you need to do the following on the remote server:
echo “$USER ALL=(ALL:ALL) NOPASSWD: ALL” | sudo tee /etc/sudoers.d/$USER
How to configure sshdump:
You can find sshdump on the main screen after startup or at capture, options (see below)_
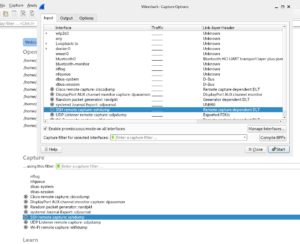
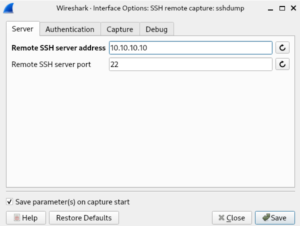
Click on the settings button left from sshdump, and fill the servername or ip address. In my case 10.10.10.10. The remote server port is probably 22 (default tcp port ssh).
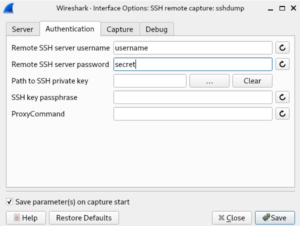
Click on the Authentication tab and enter your username en password. In my case username = username and passwqord = secret
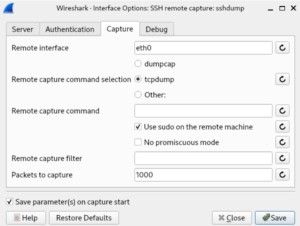
Next click on the capture tab and enter the interface to capture from, select dumpcap, tcpdump or something else to capture on the remote server. Select sudo in case you need elevated rights on the remote system. It’s highly recommended to enter a remote capture filter to reduce the number of packets send from te remote server towards the client. First of all you don’t the capture the ssh traffic between the ssh server and the client. Keep in mind, if the througput through eth0 is 1 Mbps up and down, the server will send 2 Mbps of traffic towards the client. Thus enter a remote capture filter!!!
Click on save and start the capture!